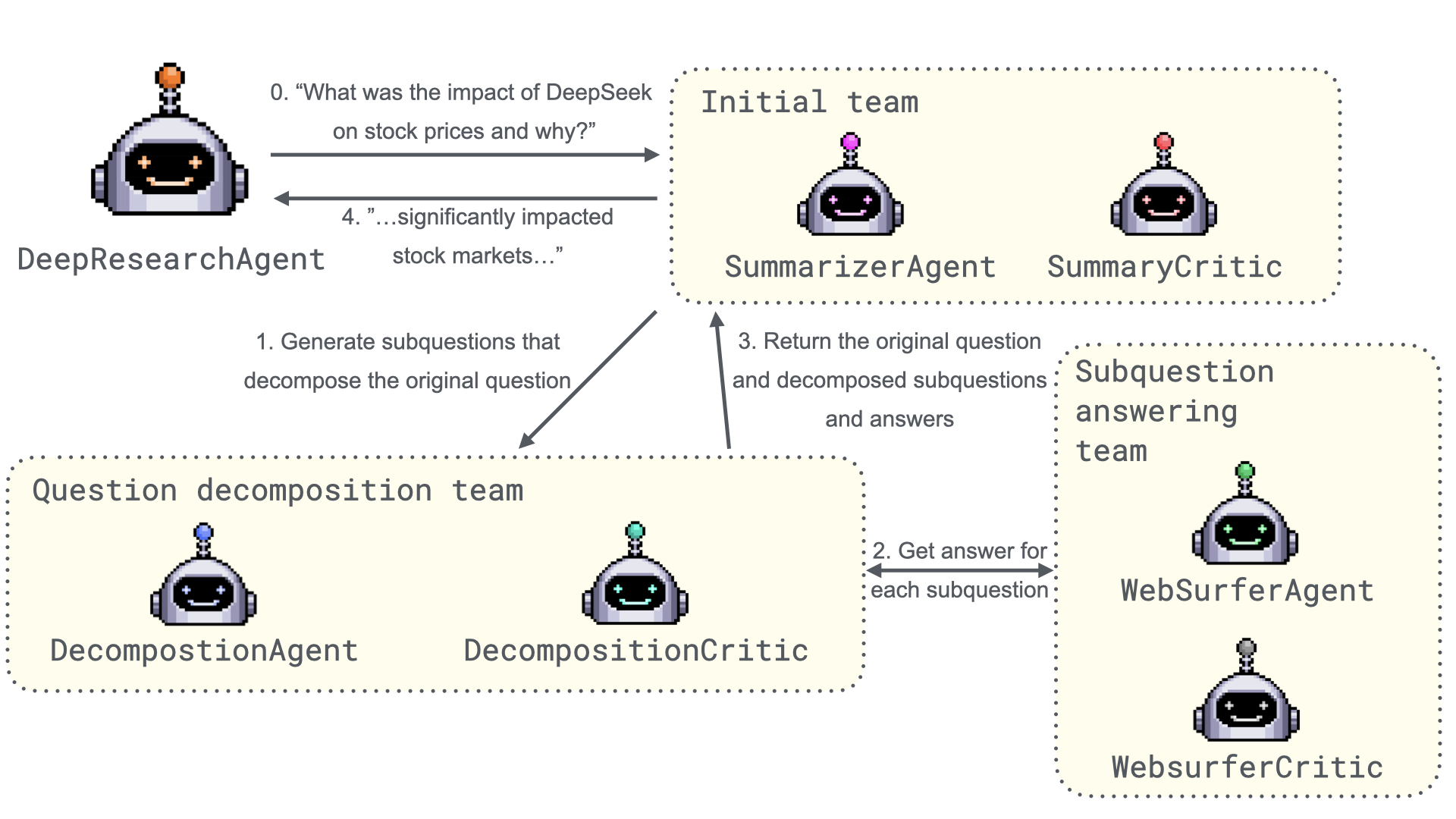
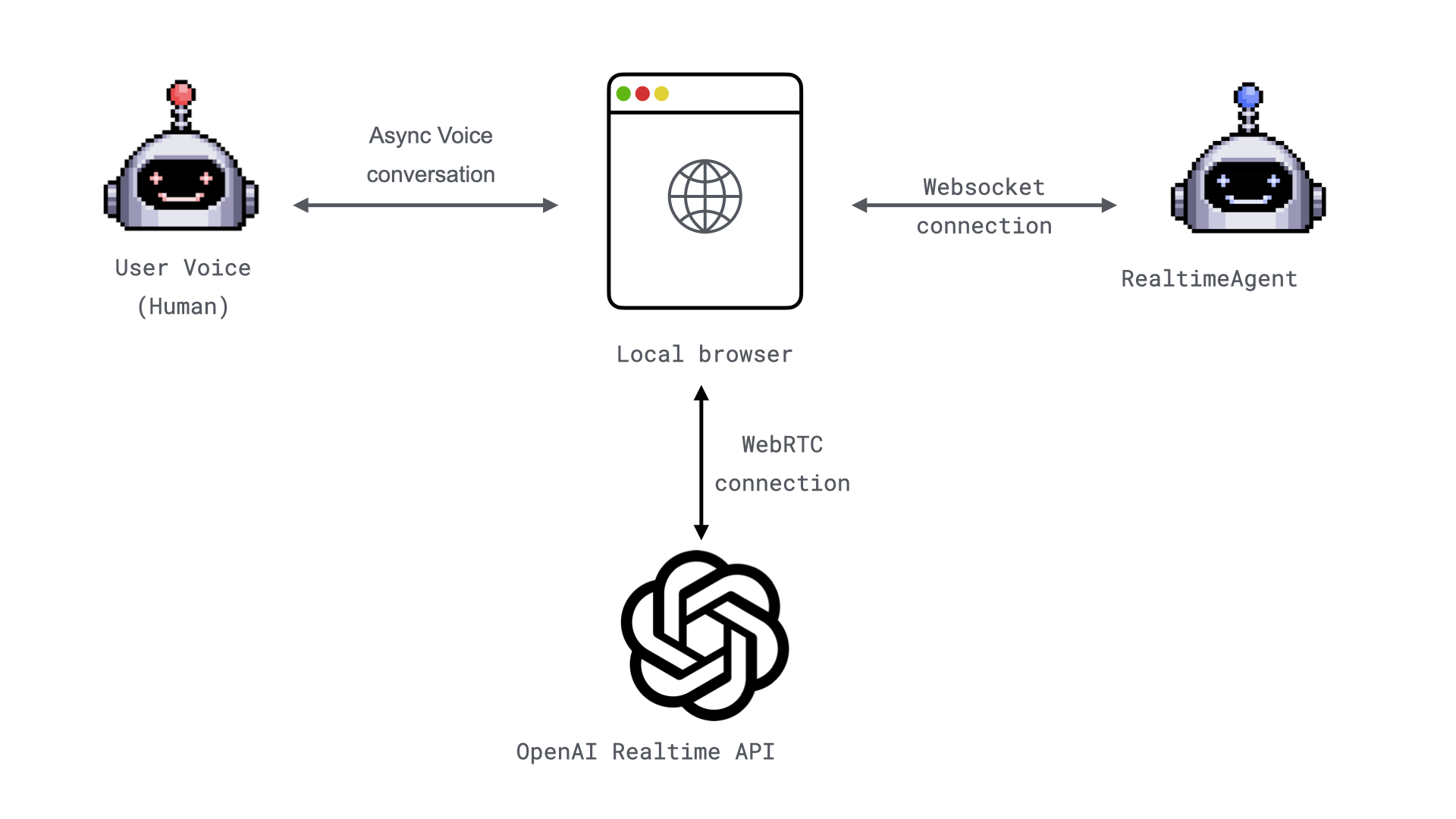
The Myth of Reasoning

TL;DR
- Human reasoning is often mischaracterized as purely logical; it's iterative, intuitive, and driven by communication needs.
- AI can be a valuable partner in augmenting human reasoning.
- Viewing AI as a system of components, rather than a monolithic model, may better capture the iterative nature of reasoning.
One major criticism of AI today, including the state-of-the-art LLMs, is that they fall short in reasoning capability compared to humans. This criticism often stems from a fundamental misunderstanding of how human reasoning actually works. We tend to hold up an idealized image of human thought – rational, logical, step-by-step – and judge AI against this standard. But is this image accurate?